Within an ACL, each line can pass or fail based on any combination of:
- IP address / mask
- port number (TCP/UDP)
- TCP flags
- ICMP type and code
- BGP ASN (if configured as an export option)
- IP Type-of-Service (DSCP, IP precedence or a simple number)
- next-hop IP / mask
- exporter IP / mask
- input or output interface
- Number of packets or bytes
- Duration of flow
- Average bytes per second or packets per second
- Average packet size
- The success of another ACL within the past n seconds
Below are several ACL examples.
simple:
ip access-list extended HTTP permit tcp any any eq 80 reverse permit tcp any any eq 443 reverse
ip host-list @local 10.0.0.0/8 172.16.0.0/12 192.168.0.0/16 ip access-list extended Internet_HTTP deny tcp host @local host @local permit tcp host @local any eq 80 reverse permit tcp host @local any eq 443 reverse
ip host-list @SAP 10.1.2.15 10.1.3.15 ip access-list extended Columbus_SAP_on_backup_path permit ip any FastEthernet0/0 host @SAP reverse exporter Rtr3
ip access-list extended YouTube permit ip any 36561 any reverse # YouTube is BGP ASN 36561
ip access-list extended IPT_g711 permit udp any gt 1023 any gt 1023 dscp ef kbps range 76 84 seconds gt 1 # g.711 should be ~80 kbps of high-port UDP for 1+ seconds
ip access-list extended EPM permit tcp any ge 1024 any eq 135 dynamic EPM flow %MSRPC timeout 1 ip access-list extended MS_RPC permit tcp any any eq 135 reverse permit tcp host $srcip ge 1024 host $dstip ge 1024 flow %MSRPC reverse
ip host-list @SAP_Servers 10.1.2.15 10.1.3.15 ip host-list @AD_Servers 10.1.2.5 10.1.3.5 10.1.4.5 ip host-list @Proxy_Servers 10.2.0.5 10.2.0.6 10.3.0.5 10.3.0.6 ip access-list map CategoryMap SAP @SAP_Servers ActiveDirectory @AD_Servers Internet @Proxy_Servers Voice @Voice_Servers @Voice_Gateways Epic 10.3.6.0/24
Categories are grouped together to create an ordered "view" which is then applied to one or more exporting devices. Multiple views can be used on the same device (e.g., it's common to have summary and detailed views of the same data). The number of categories is unlimited, though the quantity and order of categories does impact performance.
For more info on the ACL syntax, data rendering, and other configuration options, please read the PDF documentation.

This butterfly view may seem confusing at first, but it's a very practical way to display many traffic categories in both inbound/outbound directions. Naturally, you can generate simple single-axis graphs as well, as well as export the raw graph data to csv/Excel for manual manipulation.
Data is aggregated at one-minute resolution, by default. For example, here is the previous graph zoomed in to 8:00 - 10:00 am:

One-minute resolution is ideal for most enterprises since it closely matches the human factor of the end user's tolerance / patience. E.g., most users won't notice or be concerned by occasional short periods of slowness but, if the impact is a minute or more, it's almost guaranteed that they'll be unhappy.
The default aggregation can be lowered to one second and coupled with flexible netflow's one-second active flow timeout to produce amazingly precise graphs. However, the precision comes at a signifcant CPU/disk cost. If your goal is microburst policing, Netflow is really not the right tool for the job.
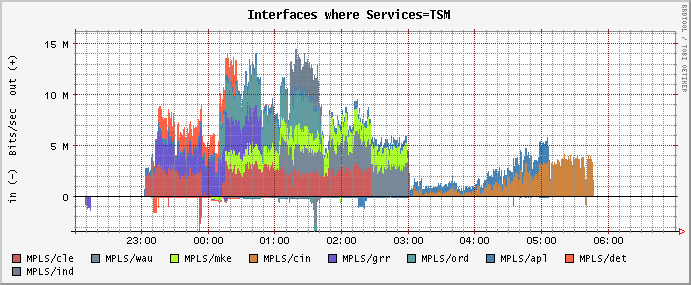
The graphs above show traffic categories for a router interface. You can also flip this around. E.g., the following graph instead has the single traffic category "TSM" (disk backup) broken out by interfaces named "MPLS/cle" (Cleveland), "MPLS/wau" (Wausau), etc.
In addition to traffic volume, Webview also reports on flows, packets, and concurrently active IPs. For example, you might be interested to know what the average bandwidth need is per active user of a certain application. The following report shows that each user of "Internet_HTTP" needs about ~30 Kbps when measured over a business week (8am - 5pm, Monday - Friday):
| Maximum bps | Average bps | |||||
|---|---|---|---|---|---|---|
| Date | Interface | Category | In | Out | In | Out |
| Mon Apr 14 2008 | LAN/apl | Internet_HTTP | 27,049 | 154,515 | 3,979 | 23,660 |
| Tue Apr 15 2008 | LAN/apl | Internet_HTTP | 62,212 | 122,788 | 6,778 | 18,697 |
| Wed Apr 16 2008 | LAN/apl | Internet_HTTP | 46,705 | 235,215 | 4,974 | 24,456 |
| Thu Apr 17 2008 | LAN/apl | Internet_HTTP | 46,584 | 312,958 | 5,161 | 30,668 |
| Fri Apr 18 2008 | LAN/apl | Internet_HTTP | 23,755 | 213,472 | 4,880 | 45,318 |
The graphing engine is very flexible (possibly too flexible!):

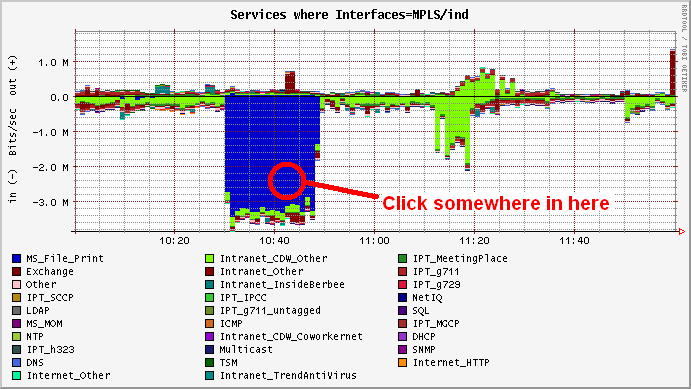
Leads to this...
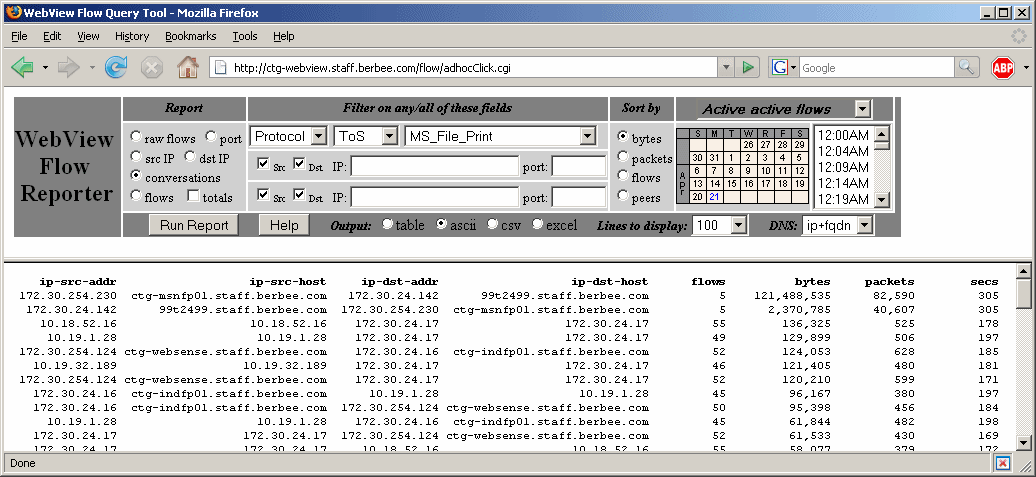
This view goes after the raw flow data, which is generally kept for at least 4-8 weeks (depending on available disk space).
The raw flow data available for reporting goes back in time as far as disk space allows. Most small to medium enterprises find that 30 GB is adequate for a month of data. Larger networks can use many terabytes.
Filtering options:
- Protocol: TCP, UDP, ICMP, VPN, Other
- ToS / DSCP / precedence / ECN
- TCP/UDP port number
- IP address or subnet
- User-defined traffic category (using the Cisco ACL syntax described earlier)
- Interfaces (names, descriptions, multiple router interfaces allowed)
- Free-form filters on byte count, packet count, bps, pps, ToS/DSCP, nexthop, tcp_flags
- Logical expressions allowed (OR and AND NOT)
Reporting options:
- Type: Raw - a simple chronological dump of raw flow data. By default, this includes IP addresses, port, protocol, DSCP, TCP flags, start time, duration, and the packet/byte counters.
- Exporters and interfaces - adds fields showing the exporter and its SNMP interface descriptions
- Routing - adds nexthop field and routing prefix length
- ASN - adds BGP ASN fields.
- Type: Connection - passes the flow data through a TCP/UDP connection engine that stitches the flow data back into a bidirectional connection, with the client and server IP's clearly identified.
- Simple - the basic report displays the client and server IP/port numbers, duration, client-to-server (c2s) and server-to-client (s2c) byte and packet counters.
- Multihop - the multihop report displays each connection as it is seen by multiple netflow collection points. For example, if a TCP flow goes across a data center router and a branch office router, this will show the connection from both perspectives. This is very handy when looking for packet loss and ensuring end-to-end QoS markings. This is a VERY cool feature!. See an Example report
- Type: Flow - this is the standard flow reporting engine.
- IP - keys off of every IP (source or destination)
- Src - keys off the source IP -- this enables the peers counter which shows how many destination IP's each source is sending packets to.
- Dst - keys off the destination IP -- this enables the peers counter which shows how many source IP's are sending packets to the destination.
- Port - keys off the source/destination port number.
- Peers - keys off each source & destination IP pair
- Flows - keys off each 5-tuple - protocol and source/destination IP&port
- w/totals - this checkbox will display totals for the entire range, even if only the "top 100" or so items are shown.
- Type: Other - miscellaneous reports
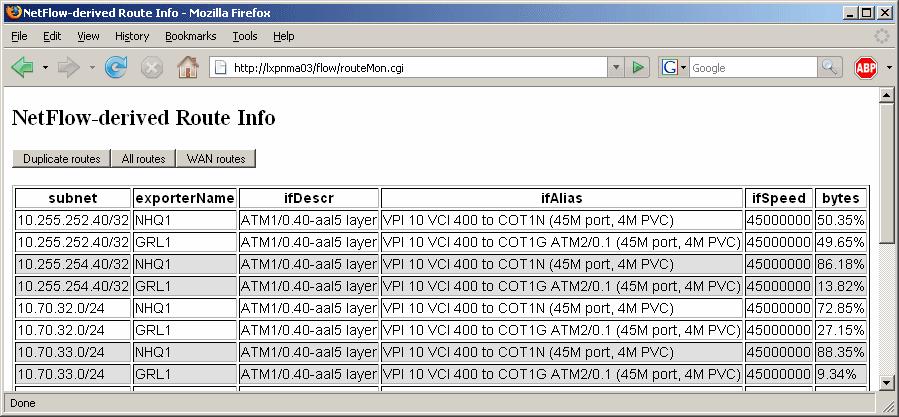
- Exporters - shows a list of all exporters and the volume of flow data received from each, after applying any of your filters. This also identifies one-way interfaces, which can be useful to identify misconfigured netflow. Note that the exporters report from the webview home page shows more details of a sysadmin nature, but does not have any filtering ability.
- BGP ASN - generates a flow report by autonomous system numbers (ASN), which aren't often enabled in netflow collection.
Other options:
- Output: Excel, CSV, ASCII, or HTML table
- Input: one or more time-stamped raw flow input file(s). Multiple flow directories are allowed.
- DNS: fast and non-blocking (never delays a report more than 5 seconds).
- Sorting: bytes/packets/flows/peers/duration/chronology. Peers is a count of an IP's connection peers and is great for finding out who is the chattiest -- e.g., malware attempting to spread, DNS servers being hammered, etc.
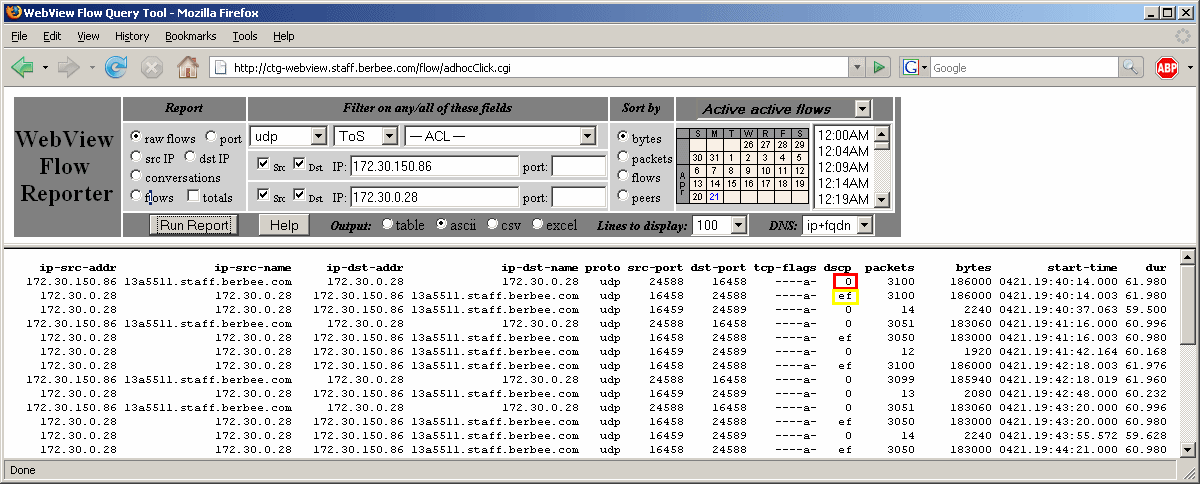
Note: The usefulness raw netflow data cannot be overstated! Many Netflow software packages aggregate the data or drop fields that don't fit their notion of monitoring. The ad hoc query tool provides a powerful interface to the raw data, the user has unlimited options for investigating this data.
Interfaces can also be aggregated and renamed. For example, say you had four routers:
Rtr1 Ethernet0/0 "Cleveland LAN" Rtr1 Serial0/0 "Cleveland MPLS T1" Rtr2 Gig0/0 "Columbus LAN primary" Rtr2 Gig0/1 "Columbus LAN backup" Rtr2 Multilink1 "Columbus MPLS 3xT1" Rtr3 Fast0/0 "Columbus LAN" Rtr3 Tunnel1 "Columbus MPLS VPN backup" Rtr4 Fast0/0 "Indianapolis LAN" Rtr4 Serial0/0.3 "Indianapolis Frame-relay T1"
'(\S+) LAN' 'LAN $1' '(\S+) (MPLS|Frame-relay|ATM|Direct|Tunnel) (\S+) 'WAN $1'
| Alias displayed in the GUI | Interfaces used in reports |
|---|---|
| LAN Cleveland | Rtr1, Ethernet0/0 |
| LAN Columbus | Rtr2 Gig0/0 and Gig0/1 and Rtr3 Fast0/0 |
| LAN Indianapolis | Rtr4 Fast0/0 |
| WAN Cleveland | Rtr1, Serial0/0 |
| WAN Columbus | Rtr2, Multilink1 and Rtr3, Tunnel1 |
| WAN Indianapolis | Rtr4, Serial0/0.3 |
The beauty of this approach is that GUI interface is stable and easy-to-navigate, even though the underlying network routers and interfaces may change frequently. It also lets multiple interfaces be easily aggregated together.
However, for those who don't fit this mold, Webview has full support for processing and visualizing Netflow data:
- by subnet gleaned from the exporting router's routing table
- by subnet / CIDR block defined by hand
- by source/destination IP address
- by source/destination BGP ASN
- by IP next-hop
- according to a ACL
The subnet tracking very useful when Netflow data is not available for a portion of the network. For example, perhaps Netflow is collected only from the head-end routers of an full-mesh MPLS WAN. In this case, tracking Netflow stats by subnet can provide an excellent inferred view of each remote site.
- tally the flow based on when it was received by the collector
- tally the flow based on the start, end, or middle timestamp of the flow
- distribute the flow evenly over the duration of the flow. This nicely handles flows that are long or straddle a sample interval. E.g., a four minute flow that starts at 07:58:00 and ends at 08:01:59
This last approach has several advantages:
- sample sizes can be smaller than the capture file duration. The Step in webview is the size of each sample interval, and it can be set anywhere from 1 second up to the capture file size (normally 5 minutes). In practice, 60-second samples provide an excellent balance between CPU/storage and being able to see full impact of traffic spikes.
- flows can be delayed. Even in a simple network, a collector won't receive a Netflow packet until several seconds after the flow finished. In a complex network with multiple collectors, it might take minutes or hours for the flow to be gathered at a central point for processing.
- flows can be replayed. E.g., if you change the rendering configuration, it's easy to replay the last month of data through the new configuration.
- an aggressive active flow timeout is unnecessary (i.e., 'ip flow-cache timeout active 1'). In fact, webview can be configured to handle the default timeout of 60 minutes, and the graphs will look just as good as with a 1-minute timeout.
- it guarantees consistent, accurate reporting, even on time-challenged virtual machines. Some VM's seem to have problems with their real-time clocks, leading to "5-minute" flow files that contain anywhere from 3 to 8 minutes of data. That's no problem when the timestamps are used.
Flow collection
Webview uses a modified version of Damien Miller's flowd (http://www.mindrot.org/projects/flowd/) netflow collector.- Very high flow rates (tested to over 50,000 flows/second)
- Tested up to a thousand concurrent exporters
- Handles out-of-order netflow packets -- something that no known commercial product does
- Supports multicast listening, which is useful for redundancy
- Compatible with samplicator, a utility that can replicate netflow traffic to multiple collectors.
- Supports v1/5/7/9 netflow data. v9 netflow is supported, but only traditional v5 netflow fields are stored to disk. All other flow fields are discarded. Hopefully this will change soon!
Robust exporter management
- Webview's goal is ZERO maintenance regardless of the number of netflow exporters.
- New exporters are auto-discovered using a list of SNMP v1/v2/v3 parameters (optionally bounded by netmasks).
- Router upgrades? IP address changes? New interfaces? No problem! Webview gracefully handles exporter moves/adds/changes.
- Redundant pairs of router? You can work with them as a single device.
- Comprehensive reporting on the health of all exporters
(See sample of an exporter status report showing 600+ exporters):
- SNMP reachability
- export version and packet counters, including lost and duplicate packets
- flow export volume
- network traffic volume on each exporter interface
- exporter clock health -- out-of-sync, skewed, or totally fubar.
- exporter misconfigurations:
- active flow timeouts
- one-way interfaces
- duplicate flows
Soapbox on why managing your flow collection is really importantHere are some real-world examples of Netflow data mismanagement:
- Network traffic spikes create congestion that causes Netflow export packets to be dropped. As a result, the network admin sees no evidence of the spikes!
- Multiple copies of each netflow packet are finding their way to the collector. This can happen when a router has multiuple exporters defined or when intermediary collectors are misconfigured (e.g., using netflow relay, forwarding, or chaining features of commercial packages).
These problems are difficult to notice without a good view of collection health. My experience is that commercial Netflow products are weak in this regard. When given out-of-order or duplicate netflow packets, they either don't notice anything is wrong, or they report erroneous findings (billions of drops, for example).
Flow processing
- native SMP (symmetric multiprocessing) for environments with multiple exporters
- processing speeds of 5-50k flows/second per vCPU, depending on configuration complexity
- rrdcached-compatible to optimize disk I/O
- advanced clock synchronization
- Webview has been battle-tested in several demanding multi-national and Fortune 100 environments
- Flow-collection is handled by Damien Miller's flowd (http://www.mindrot.org/projects/flowd/), with modifications. All modifications have been submitted back to the flowd project and will eventually be merged.
- Flow-reporting and filtering is handled by Mark Fullmer's flow-tools (http://www.splintered.net/sw/flow-tools/). Although a bit old, flow-tools still does some things better and faster than any other package.
- A javascript web calendar comes from DHTMLX (http://www.dhtmlx.com/docs/products/dhtmlxCalendar/).
- Perl! Webview Netflow Reporter is almost entirely written in the Perl scripting language. Perl offers great flexibility, rapid development, easy modification, and high performance.